
Copy Protection for PDF, Video and Web Page Media
Copy Protection and Copy Protect Software
The term Copy Protection Software has been around since the early days of software development. It was originally used to describe methods by which software and digital content could be secured against unauthorized copying and distribution. As every software author quickly discovers, without strong content protection software, applications and files are often forwarded to others or even offered as free downloads online, depriving creators of revenue and discouraging further innovation.
The earliest forms of software copy protection required a key code that was provided only to licensed users. Entering this key activated the program, while unlicensed copies would run only in limited or trial mode. However, license keys could still be shared among friends, and while companies would avoid being flagged as distributors, there was little to stop casual users. Legal action was costly and rarely effective, making stronger copy protection solutions necessary.
To combat this, the hardware dongle was introduced. A dongle was a small physical device that connected through a printer or USB port and served as proof of ownership. Without the dongle, the software would not run. Although inconvenient, dongles significantly reduced piracy and are still used today in specialized industries. However, with the rise of the internet, many companies turned to more advanced digital rights management (DRM) and copy protection systems that could safeguard distribution online.
Exploiting Copy Protection

It seems that for everything created, there is always someone trying
to exploit or break it - and copy protection software is no exception.
To bypass license validation, hackers often reverse engineer applications
and create key generators that produce fake activation codes. This
undermines the purpose of legitimate software copy protection solutions,
allowing unauthorized users to access premium software without payment.
No program was safe from these keygens until stronger measures were introduced
in the early 2000s. For example, Microsoft shifted from simple license
codes in Windows 2000 to online activation with Windows XP, where each
installation had to be verified before the license expired. This innovation,
often referred to as digital rights enforcement, made it much harder
for pirated licenses to spread freely. Computers were increasingly fingerprinted
and tagged to specific license owners, reducing the effectiveness
of piracy.
Today, protecting software and digital content is a complex but
essential business. At the same time, there is strong motivation to bypass
even the most advanced protection methods, as piracy continues to be lucrative
for hackers and a threat to publishers. Software developers who rely on
third-party copy protection and DRM software must rigorously test
these systems to ensure they actually prevent unauthorized use, because
even a small weakness can be exploited at scale.
Copy Protection for Digital Media
 If digital media such as videos, audio files, and eBooks could
be securely copy protected, the livelihood of artists, publishers, and
producers would be far better safeguarded. Unfortunately, digital media
has suffered the same fate as the software industry: whenever a new copy
protection solution is introduced, hackers quickly rush to find ways
to exploit it.
If digital media such as videos, audio files, and eBooks could
be securely copy protected, the livelihood of artists, publishers, and
producers would be far better safeguarded. Unfortunately, digital media
has suffered the same fate as the software industry: whenever a new copy
protection solution is introduced, hackers quickly rush to find ways
to exploit it.
Because DVDs are played on so many different types of players, it has been
virtually impossible to enforce strong DVD copy protection. Some
media distributors attempted to embed copy protection into hidden tracks
on disks, but these methods were quickly circumvented. The only disks
that have been reliably secured are video games designed for proprietary
platforms like Wii and Xbox, where the hardware itself validates that
the disk is original and not a duplicate.
For mainstream video and music publishers, limiting distribution to proprietary
players is rarely feasible. Instead, they often rely on mass distribution
strategies, accepting a degree of piracy while hoping that overall sales
volume provides enough return. This is why more advanced video copy
protection software and digital content protection systems - such
as encryption combined with digital rights management (DRM) - are
now critical for preventing unauthorized copying and preserving revenue
streams.
Copy Protection for Web Content
 There has traditionally been less demand for website copy protection
because online content such as images, articles, and graphics was often
considered less valuable than music or video files. Losses from piracy
of text and images seemed insignificant in comparison. However, as businesses
and educators increasingly rely on the web to distribute premium content,
the need for web content protection software has grown rapidly.
There has traditionally been less demand for website copy protection
because online content such as images, articles, and graphics was often
considered less valuable than music or video files. Losses from piracy
of text and images seemed insignificant in comparison. However, as businesses
and educators increasingly rely on the web to distribute premium content,
the need for web content protection software has grown rapidly.
The challenge lies in securing highly portable media that can be accessed from
numerous devices and web browsers - most of which are designed to make saving,
copying, or downloading content easy. Standard methods like right-click
disable scripts are easily bypassed, which is why true copy protection
for websites requires more advanced solutions.
Effective web copy protection technologies emerged later than those
for software or media files, but they faced the same constant battle against
hackers and those determined to exploit weaknesses. Millions of users
worldwide are interested in finding ways to bypass copy protection techniques,
making robust and innovative approaches essential.
ArtistScope has been a pioneer in this field, leading innovation in copy
protection software for web content since 1997. Their early research
began with image encryption and has since evolved into advanced systems
capable of locking down entire websites. Unlike basic plugins, ArtistScope
solutions such as ASPS (ArtistScope Site Protection Software) secure
the browser-to-server stream itself, leaving no avenue exposed for copying.
While some methods may bind protection tightly to specific hardware for
maximum security - a level that may be too strict for casual publishing - these
solutions provide unmatched protection for publishers who require the
highest level of digital security.
Copy Protection for Documents
 Again, document protection has been less important to the
major developers. Documents are difficult to protect using
a single solution that satisfies everyone's requirements. Some
companies have developed sophisticated content servers to
manage DRM tokens that are distributed with protected
documents but while these solutions have been user
friendly, they have also been easily exploited.
Again, document protection has been less important to the
major developers. Documents are difficult to protect using
a single solution that satisfies everyone's requirements. Some
companies have developed sophisticated content servers to
manage DRM tokens that are distributed with protected
documents but while these solutions have been user
friendly, they have also been easily exploited.
Digital Rights
Management (DRM) is a term that was coined to
differentiate between the protection of digital media and
the protection of software, although when you get down to it
and do it properly, there is really no difference at all.
Up until recently, DRM tokens took the form of digital certificates
associated with registry keys that were distributed with the
document. But because both the certificate and the means of
validating it (the reader) is downloaded to the user's
computer where it is vulnerable to mischief, the hacker has everything he needs and one only
has to perform a web search on the topic of "how to remove
DRM" to realize how popular that activity is.
ArtistScope DRM does not
use tokens or document readers that can be exploited.
The Future of Copy Protection
ArtistScope has been at the forefront of the copy protection industry since its early days, introducing some of the very first digital content protection solutions for use on the Internet. Over the decades, the company has continued to innovate while surviving the constantly changing web environment and the vulnerabilities introduced by new platforms, browsers, and services. One of the most persistent risks remains the ability to copy, plagiarize, and redistribute digital content, threatening the livelihood of creators worldwide.
With every new development in technology, there are always individuals or groups eager to exploit it. Whether through reverse engineering, the creation of unauthorized tools, or plagiarism, attackers consistently look for ways to undermine existing copy protection software. The industry itself is not immune: competitors sometimes engage in intellectual property (IP) theft, repackaging ideas, rewriting documentation, or even stealing targeted keywords to market their own imitations.
The future of copy protection and DRM software will depend on continuous innovation, stronger encryption, and more advanced methods to block unauthorized copying - especially against sophisticated threats like screen capture and automated piracy tools. As digital media consumption grows across e-learning, entertainment, publishing, and corporate sectors, demand for reliable content security solutions will only increase. Companies that can provide proven, end-to-end protection - like ArtistScope - will remain essential partners for anyone serious about safeguarding their intellectual property.
Key Features of Copy Protection Software
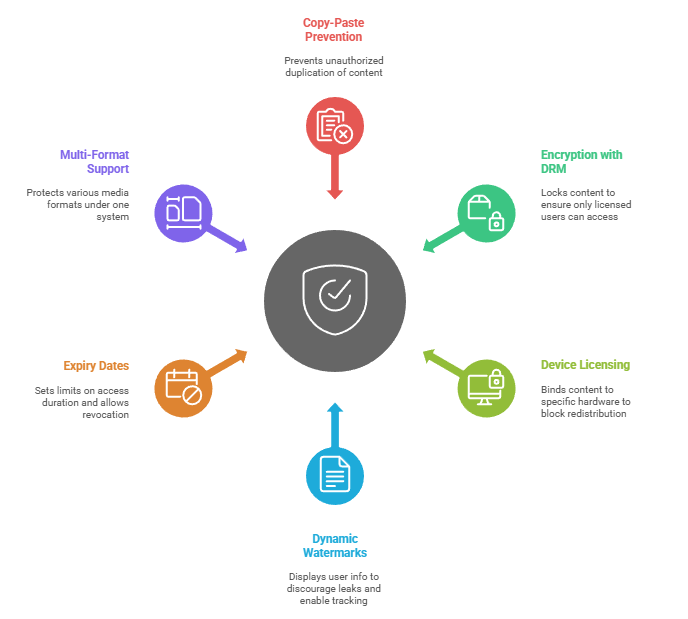 Modern copy protection software goes far beyond basic password protection or right-click disable scripts. To provide true content security, robust solutions now include:
Modern copy protection software goes far beyond basic password protection or right-click disable scripts. To provide true content security, robust solutions now include:
- Prevention of copy-paste, printing, and screenshots - ensuring that files cannot be duplicated or shared without authorization.
- Encryption with DRM controls - locking documents, videos, and web pages so that only approved subscribers can access them.
- Device and user-based licensing - binding content to specific hardware or user accounts to block redistribution.
- Dynamic watermarks - displaying user information on documents or videos to discourage leaks and enable tracking.
- Expiry dates and revocation - setting limits on access duration and remotely revoking access when required.
- Multi-format support - protecting PDF, video, images, HTML, and other media formats under one system.
- Multi-platform support - be readable across all OS and devices including Windows, Mac, Linux, iOS and Android phones.
These features make content protection software essential for creators, educators, and organizations that need to prevent unauthorized distribution and preserve their intellectual property.
Who Needs Copy Protection Software?
 Copy protection solutions are valuable across industries where
digital media and documents form the core of business operations. Key
users include:
Copy protection solutions are valuable across industries where
digital media and documents form the core of business operations. Key
users include:
- Publishers & Authors - safeguard eBooks, whitepapers, and research documents from illegal copying and file sharing.
- Educators & eLearning Providers - protect online courses, training videos, and educational PDFs distributed to students.
- Enterprises & Corporations - secure internal reports, client files, and confidential presentations against data leaks.
- Media Producers & Streaming Services - prevent piracy of videos, music, and subscription-based content.
- Web Publishers & Membership Sites - lock down premium articles, photo libraries, and online resources behind paywalls.
Whether you are a content creator, business, or educational institution, copy protection and DRM software ensures your valuable assets are distributed securely while preventing misuse, piracy, and plagiarism.
Frequently Asked Questions About Copy Protection Software
Q1. What is copy protection software?
Copy protection software is designed to prevent unauthorized copying, sharing, or distribution of digital content such as PDF, video, audio, images, and web pages.
Q2. How does video copy protection software work?
Video copy protection software encrypts video files and restricts playback to authorized devices or players, while blocking screen recording tools.
Q3. Can PDF copy protection stop printing and sharing?
Yes. PDF copy protection software with DRM ensures that documents cannot be copied, printed, or shared without permission
Q4. What's the difference between DRM and copy protection?
DRM controls access rights (who can view, how long, etc.), while copy protection prevents actual copying (print, screenshot, or save).
Q5. Who needs copy protection software?
Publishers, educators, e-learning companies, software developers, and digital media businesses all rely on copy protection to safeguard their intellectual property and revenue.
Copy Protection Solutions That Do Work
The following list includes applications that were developed by ArtistScope that are 100% original innovations. These are also the most secure solutions available/possible today:
- ArtistScope DRM - document rights management for PDF documents
- ArtistScope Site Protection Software (ASPS) - copy protected website to browser stream
- ArtistScope Web Reader - custom browser for viewing copy protected websites
- CopySafe PDF Protector - capture safe copy protection for PDF documents
- CopySafe Video Protection - capture safe copy protection for avideo
- CopySafe Web Protection - capture safe copy protection for all web content
- SafeGuard Media - copy protection for shared hosting sites