Copy Protecting PDF : Copysafe PDF Protection
- File vs Image Protection
- DRM & Copy Protection Features
- PDF Document Preparation
- Delivering Copy Protected PDF
- Embedding Protected PDF on Web Pages
- Return to the INDEX
📖 File Protection vs Image Protection
The two (2) main areas to defend are:
- File Protection - is prevention of PDF file copy is the prevention of PDF file duplication, and while preventing the copy of the PDF file itself for redistrubition is impossible, it is possible to lock the contents of the PDF file so that it cannot be opened except when an author's conditions are met.
- Image Protection - is prevention of copy of the contents of the PDF file while it is open and on display.
PDF File Protection
Preventing PDF files from being opened is the only way to prevent file duplication because any such file copy will only create another file that still cannot be opened. Until such time that the file can be opened, its contents will remain secure, ie: they cannot be read, cannot be printed, and nothing can be copied.
To prevent PDF files from being opened the contents of the PDF document need to be encrypted, and remain encrypted until such time as the author's conditions are met. Many brands of PDF Protection Software have been based on the Adobe PDF format mainly because they need to use the Adobe Reader to properly display PDF. But security provided by Adobe PDF reader is very weak and easily exploited because while encrypting the PDF by using a third party software the PDF will no longer be readable in Adobe Reader. Even Adobe's own encryption is easily exploited and one only has to see how easy it is to extract PDF passwords from Adobe PDF documents to realize that the best document protection comes from using encryption that only a proprietary reader can decrypt.
The methods of file protection used for locking PDF are:
- Password Protection - requires entering the correct password before the PDF file will open to display its contents.
- DRM - digital rights management (DRM) provides access rights control by requiring the author to validate their permission to open the PDF file. Such validation can be provided by refering to a token file that has been saved to the same location as the PDF, or call-to-home checks where the PDF document looks up server records for IP/network approval or fingerprint checking, ie: checking online records of an author's approved list of computer fingerprints or computer identitities.
Copysafe PDF Protection software provides the option of using either Password Protection or DRM. The Password Protection is much more secure because the Copysafe PDF Reader is not a generic reader and being such, cannot be easily decompiled to extract passwords like with most other "protected" PDF readers. The DRM provided by Copysafe PDF Reader is second to none, enabling author's total control over who and when a PDF document can be opened and for how long it will remain accessible. Copysafe PDF pioneered call-to-home validation for PDF instead of using token files that could be duplicated and shared.
Preventing a PDF file from being opened is the first frontier. Next comes the prevention of copy of its contents when it is open and on display.
PDF Image Protection
Without image protection, once a PDF file is open and on display, its contents can be screen captured and recorded, or even printed. The methods to control that are:
- Save Document - document readers usually provide options for Save As which enable the user to save the file by name to a variety of file type options.
- Print Document - when printing is allowed, the user can print off an unlimited number of copies.
- Print To File - when printing to network printers is allowed, a user can not only print, but also send it to file converter software running as a "print driver" that can convert PDF to any type of file. For example an encrypted/protected PDF can then be converted to a normal PDF for unauthorized distribution.
- Copy-n-Paste - By highlighting text and images users can copy them to the clipboard for later pasting into other documents, or drag them to the desktop.
- Screen capture and recording - by using PrintScreen a user can take screenshots of images and whole pages, or screen record the process of flipping through its pages.
- Remote recording - by using a virtual destop a user can view the desktop displaying the document from another desktop, one that is not limited by the controls applied to desktop on display.
Working Scenarios
Whether managing subscriptions for online courses or keeping corporate data safe within a inhouse network, the two main working scenarios are:
- Desktop Reading - where PDF documents are downloaded or sent by email, saved to the user's computer and viewed on the desktop using the Copysafe PDF Reader.
- Online Reading - where a user is provided a hyperlink to view the PDF online.
With Copysafe PDF Protection software both scenarios can be copy protected most securely. However for File Protection, DRM can only be applied for desktop reading because for online reading, any access controls that may be required are best provided by the web site user management (login) system (avoiding double standards and conflicts).
📖 DRM & Copy Protection Features
PDF Encryption
Copysafe PDF uses military grade encryption specially designed to not increase document file size. Copysafe PDF documents are decrypted in memeory so that PDF files stored on the user's computer or in browser cache remain encrypted and not readable by direct or otherwise unathorized means.
Domain Lock for PDF
Copysafe PDF files displayed on web pages are domain locked to the web site that owns them. This means that even if someone can download the actual .class file, it cannot be opened directly or displayed on another web site.
Copy Protection for PDF
Copysafe PDF documents are copy protected from all exploits including:
- PrintScreen and screen capture.
- Copy-n-paste and Drag-n-drop to the desktop.
- Password and data extraction.
- Save and print (unless specificall allowed).
- Send to printer drivers for file conversion.
- Optional watermark cannot be removed.
Access Rights (DRM) for PDF
The digital rights management (DRM) available as an option for Copysafe PDF documents is second to none. Protected PDF distributed by download for desktop reading can be protected by DRM to prevent file copy and image copy. File copy will be useless because anyone else trying to open the file will fail. When DRM is applied to Copysafe PDF documents only those users who have the express authorization of the author can open them and view their contents.
DRM options available authors:
- Expration by calendar date.
- Expiration by number of views.
- Expiration by number of days.
- Print limitation - off/number of printer visits.
- DRM priveleges assigned to users by ComputerID, group or DRM token.
- User and group management for class level/department assignment.
- Group sharing and whitelist for cross-level assignment.
- Total control over any changes made to document settings.
- DRM changes take immediate effect, even to documents already saved to a user's computer.
User Identification
For the purpose of managing the access rights of each individual user to open and view protected PDF and Ebooks, each user is identified by a unique computer signature (fingerprint). Once a user's device is registered in the Copysafe DRM portal their access is granted automatically thereafter for any and all entitlements. A user should only ever be prompted the first time that they open a Copysafe PDF document.
However limitations may be in place for how many computers/devices each user can use. Those limits are applied by the Author (owner) of the Group that the User or Document belongs to. Users needing to exceed their allowance or change existing device records will need Author assistance - our support is extended to Authors who in turn need to take repsonsibility for their own Users.
Group Permissions
Group management is one method of providing access rights to a Collection of PDF and eBooks. Users are assigned to Groups and users are assigned to Groups, which means that any user of a group has the right to open any PDF or Ebook assigned to the same Group.
A typical example would be having all lessons for Year One Maths in one Group and the lessons for Year Two Maths in another Group.
Group Whitelisting
Whitelisting can be used to enable a user who is a member of one Group to access the PDF and Ebooks that belong to another Group.
DRM Tokens for Ebooks
DRM Tokens can be assigned giving individual users the access rights to use an individual PDF or Ebook. DRM Tokens function independent of Group permissions.
DRM Tokens can be assigned manually from the author's dashboard, upon which an email with the DRM Token attached, login details and instructions can be sent to the new or existing user.
When anyone orders from the Copysafe Book Store, a DRM Token is created automatically and sent by email with instructions and a receipt.
Copysafe Ebook Store
The Copysafe Ebook Store is free to use by all licensed authors - anyone with a Copysafe PDF software licence and authors renting the Copysafe PDF portal for DRM.
To add a PDF or Ebook to the online catalogue, it first needs to be in an Author's document list. Once that is established, it then needs to be "promoted" to Ebook status - from the links in the document list.
There is no limit to how many Ebooks can be promoted, and there is no comission due or fees for listing Ebooks in the Copysafe Book Store. However one does need to have a PayPal account - then all transactions are between the purchaser and the author. It is then the Author's responsibility to provide support for their own Ebook sales.
Selling From Other Online Stores
PDF and Ebooks managed by the Copysafe PDF portal can be promoted, sold and distributed via any online book store. The only limitation is that the Ebook provided from their site for download may not meet their requirement if they only allow certain file types, for example, Ebooks viewable in generic Ebook readers.
However that requirement can be satisfied by uploading a placemarker to provide a notice about waiting for an email from the Author with further instructions.
After receiving a successful sale notice from that book store, authors can then create a DRM Token that will be sent from the Copysafe server.
Custom Templates
Authors can create custom templates that will be used for standard messages when sending out newsletters, delivery from online sales, and new DRM tokens.
📖 PDF Document Preparation
Document Formats for PDF Encryption
The Copysafe PDF Protector software encrypts normal PDF documents so that they can only be viewed by Copysafe applications, whether that be for desktop reading or online reading (from a web page).
However both the desktop version of the Copysafe PDF Protector software and the online version have limitations in regard to quality. Not every software that creates PDF actually uses strict PDF protocol. Some of the PDF created by some applications can only be read using their proprietary reader. Even Adobe has left the rails in that respect because some of their PDF creation tools now create PDF documents that are only readable in the latest versions of Adobe Reader.
Now that might be ok for normal PDF, but we are using Copysafe PDF Reader because we are using copy protection far superior to what Adobe is prepared to provide. That being said, hopefully the requirements for stable PDF format can now be appreciated. Other applications that convert from various file formats to PDF may also introduce compatibility problems.
If in doubt, test the PDF document using the Copysafe PDF Protector software, and if it cannot be opened or displays layout errors in the Copysafe PDF Reader, then check your output settings for the original PDF conversion. For example, if using any Adobe tools to create PDF, make sure that the compatibility setting is set for Acrobat version 8 or earlier.
PDF Creation
For Windows users, we strongly recommend using the Universal Document Converter (UDC). A free version of UDC is bundled with the Copysafe PDF Protector installer.
PDF Bookmarks
Bookmarks pointing the document from outside (linked from web web pages) do not work with Copysafe PDF documents. But bookmarks created within the PDF document should work. However that may depend on the original document writer and how those bookmarks are applied. It is best to create a test file, convert to PDF and then encrypt using Copysafe PDF Protector before adding bookmarks to the whole document.
Image Optimization for PDF
Using images that have not been optiized for use in computer documents is a common mistake. In fact photographers can be the worst offenders, because they believe that their images should be of the highest quality, which means oversized and using high resolutions that are not actually supported by modern computer monitors and screens. But it is easy for anyone to make that mistake because modern mobile phones can take photos at 300-600 DPI resulting in files sizes more than 4 MB. But by converting to 96 DPI, which is what most quality screens can display, the file size can be dramataically reduced to about 100-200 Kb.
Images dimensions are also a concern because a photo taken by a mobile phone can be 4,000 pixels wide. Most computer monitors are only about 1400 pixels wide and mobile phones will display at about 500-600 pixels wide.
By not optimizing your images, a PDF can end up being 400 MB but with optimised images it might only be about 10 MB.
File Size Limitations for PDF
While there is no limit to file size that the Copyafe PDF Protector can handle, when encrypting PDF, anything above 100 MB might slow a computer if they have limited memory resources, because unlike a normal PDF, Copysafe PDF files are encrypted and their decryption is processed in memory before they can be displayed.
PDF documents uploaded to the Copysafe PDF dashboard for DRM are limited to a maximum of 80 MB per upload. No one has ever had a problem with that limit, that is, after they checked image sizes.
At the end of the day, what an author needs to consider is the download time of the document as not everyone will have a good Internet connection. In fact mobile users may not only have limited download speed but they may also be limited in download allowance.
📖 Delivery Methods for Copy Protected PDF
Copysafe PDF documents are encrypted, and as such, should not be confused with normal PDF documents because people will try to open them using a generic PDF reader that will result in errors. So Copysafe PDF utilizes two (2) distinct file types, one for each type of distribution.
Desktop Publishing
Copysafe PDF documents for desktop reading can be made available for download or sent by email. The user can save these files to anywhere on their computer for later reference.
Copy protected PDF files for desktop reading use the .ENC file format that the Copysafe PDF Reader can decrypt and open. However care needs to be taken when providing downloads or sending as an attached file because some mail services may reject the unfamiliar file type. To avoid that from happening it is always best to send compressed files (ZIP).
Another point to watch, and your users should be forewarned, is that some mail services like GMail try to be clever and open compressed files and run them without first uncompressing the ZIP. Users should unpack a ZIP file and then open the document file directly.
Online Reading
Copysafe PDF documents for online reading are not distributed to users. Instead they are downloaded and displayed by the web pages created for them. They cannot be saved, and even if they could, they cannot be opened except for display on the web page that they were encrypted for, ie: Copysafe PDF files as .class are domain locked.
File Types
The different types of Copysafe PDF files can be identified by their file extension.
- .class - for example myDocument.class will be a copy protected PDF that can be displayed on web pages viewed while using the ArtisBrowser.
- .ENC - for example myDocument.ENC will be a copy protected PDF that can be downloaded and read using the Copysafe PDF Reader.
These file types are not interchangeable.
These file types are used because they are most compatible all round, ie: web servers should not need to have their MimeTypes configuration modified to be able to identify and know how to handle these files. Nor should anti-virus software be alarmed.
Limitations
The only difference between publishing for desktop reading and online reading, is that DRM can be applied for desktop reading (.ENC) but not for online reading (.class). That is because the Copysafe PDF Reader can call home to check the user's access rights, while protected PDF for online reading can rely on the website's user management system for access rights.
📖 Embedding Protected PDF on Web Pages
To display Copysafe PDF documents on web pages, special object code (HTML) is required to provide parameters and settings.
Hard Coding for Static Web Pages
An example of the object code for adding a Copysafe PDF .class file to a web page is as follows:
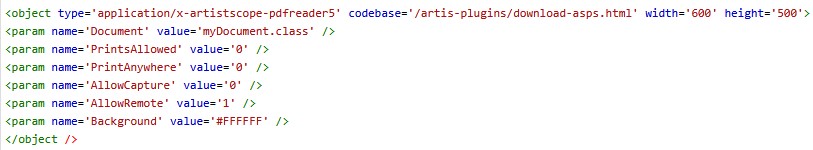
Dynamic Coding Using CMS Plugins
CMS plugins are available for DNN, WordPress, Moodle, Drupal and Joomla websites. From the CMS's web page editor one can upload/nominate the PDF file and add it to a web page at the current cursor position. The classic editor for WordPress is shown here:
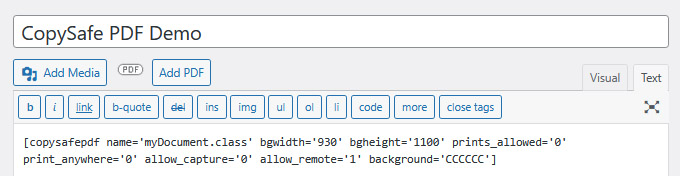
Note how a Shortcode is used as a placemarker.
Distributing To Other Pages
Once you have a template or Shortcode, it can be easily added to other pages by using copy-n-paste. Then you may only need to change the PDF file name.